CyberHoot can help secure your employees and customers
Security Awareness Training
Short and engaging videos with quizzes are sent directly to your users' inboxes.
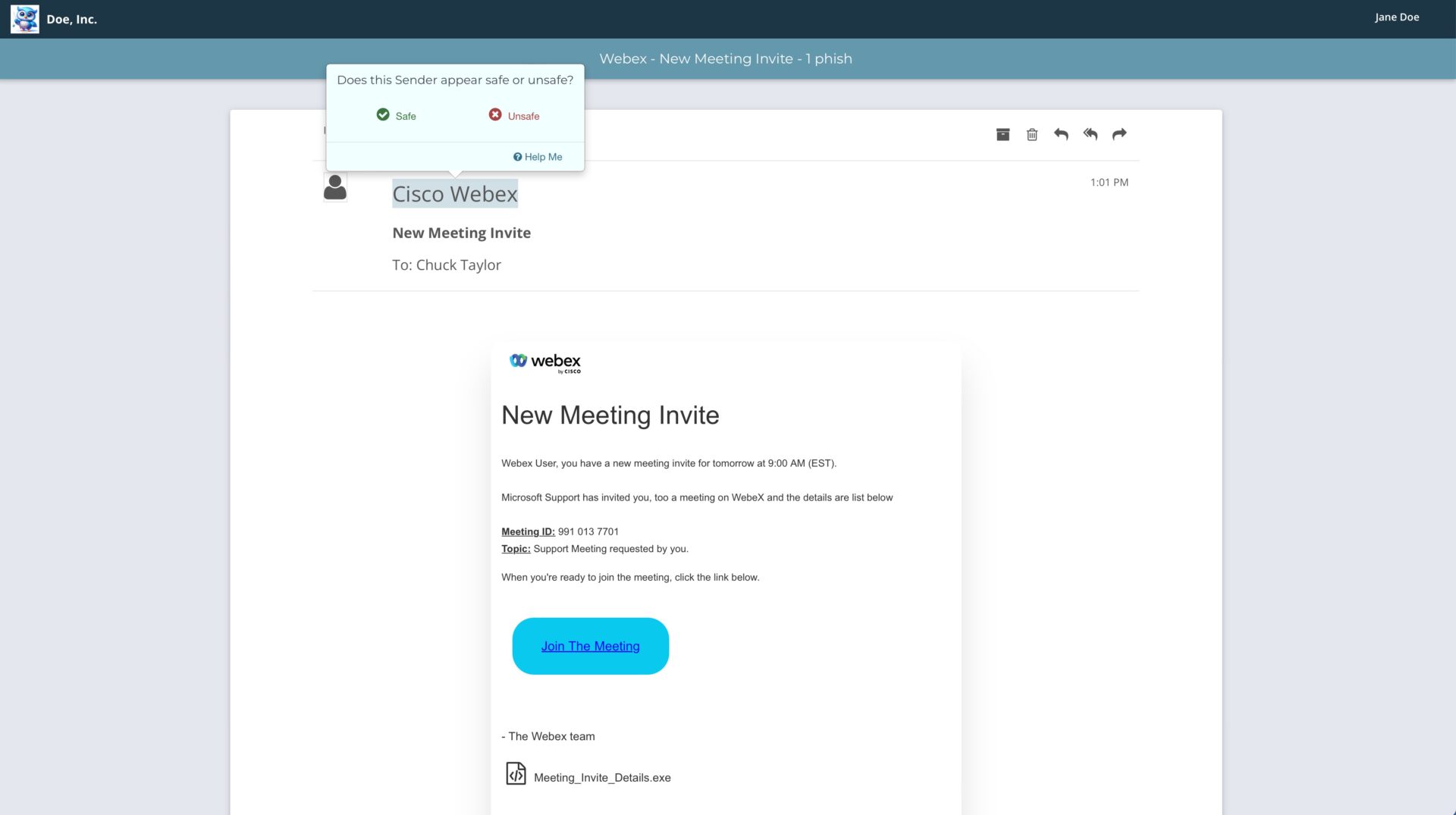
Phish Testing
Run unlimited phishing campaigns to identify users who need more training, securing any weak links.
Dark Web Monitoring
Weekly reports show when an employee's account has been exposed, allowing you to respond quickly and reduce risk.
Passwordless User Experience
No need to worry about managing user accounts and dealing with password resets. Only administrators login to CyberHoot; users receive their trainings directly to their inboxes.
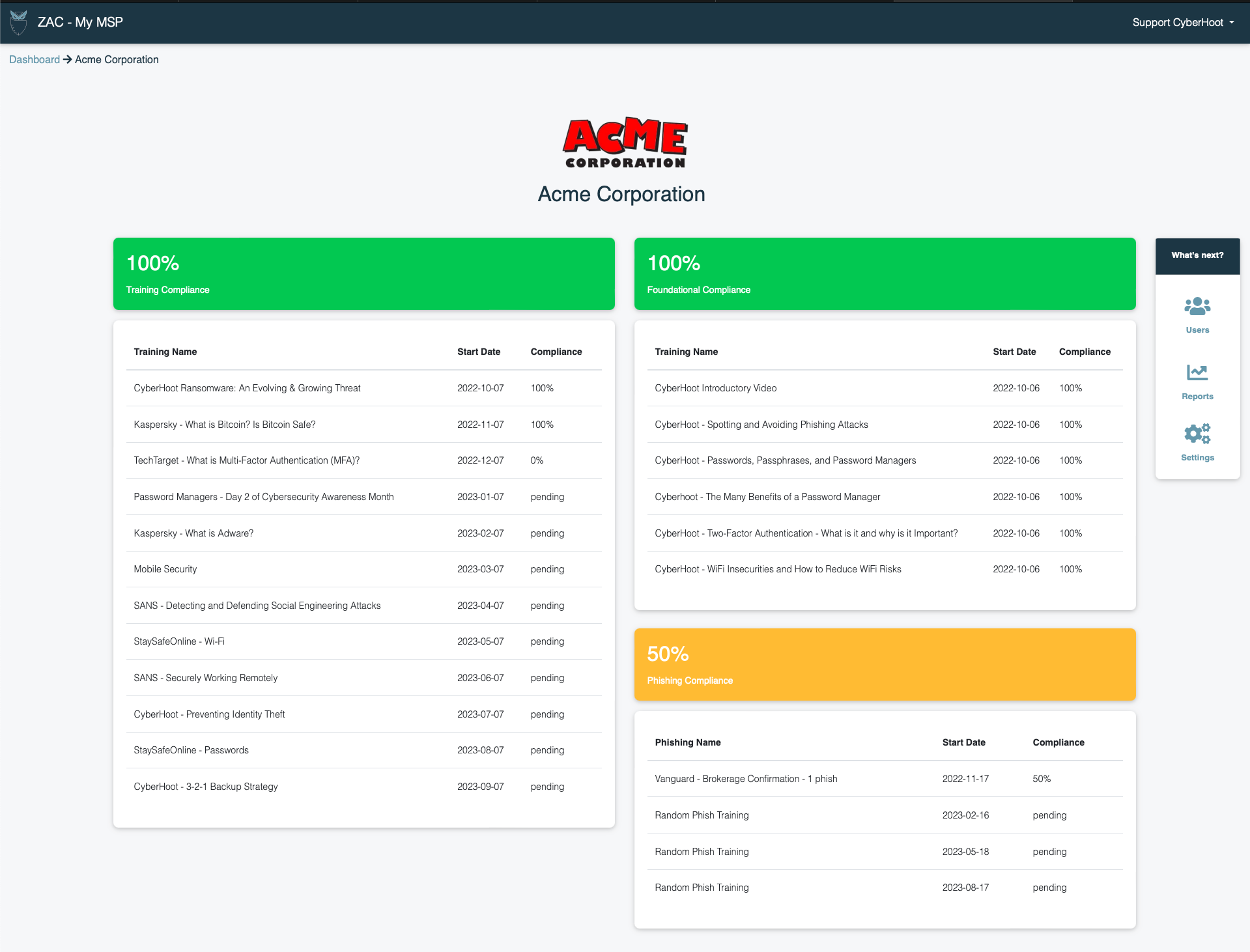
Policy Compliance Tracking
Send out policies to your users inboxes and track compliance.
Detailed Reporting
Automated reporting sends status reports directly to your inbox.
Has your personal data been exposed?
CyberHoot's free Dark Web Report can help you find out.
What's in it for you?
Per-User Pricing & Budget-Friendly Power Ups
CyberHoot Autopilot provides per-user pricing in addition to budget-friendly power ups that are a flat rate each month, no matter how many users are in the system.
Fully Automated
Once you add customers and users, monthly security awareness training and quarterly phish testing are automated, year after year. A true "set it and let it run" solution.
Whitelabeling
Fully brand your training experience and email communications. It's your offering, CyberHoot is just behind the scenes.
No Passwords to Forget
No need to worry about passwords of any kind. All trainings and functionality are provided directly to email inboxes.
No Administration
Add new customers and users in a matter of minutes. After that no administration is required. You can even setup Entra ID or Google Workspace Sync to automatically manage your customers' users.
Multi-Customer Tenancy
Support and manage an unlimited number of customers all from one spot.
Check out what our customers are saying
Tim Martin
CEO | Neoscope IT
With CyberHoot, Neoscope can support all its clients, (thousands of users) Cybersecurity educational and training needs in a single pane of glass...for Neoscope. It reduces the cost of supporting those clients due to fewer security incidents. Our clients are more secure and productive when using CyberHoot!
Heather A. Ashton
Owner | Ashton CPA
As a small business we didn’t have the budget for our own Cyber Security advisor so when we found CyberHoot, we signed up immediately. With CyberHoot, we get regular training videos with questions to challenge what we learned. We learn something new every time. I would highly recommend CyberHoot to anyone looking for this type of training.
John Mumford
Chief Risk Officer | Fellsway Group
After 9 months of CyberHoot awareness training, a Financial Management firm with $4 Billion in assets was phish tested by the Fellsway Group. They had zero (0%) employees click on the phishing test. In contrast, the exact same phishing attack had a 30% click rate at another client that had not yet done CyberHoot training. The product really proves its worth!